Intro
Hunting for malicious infrastructures and malware samples with Censys features is fascinating. In my last two articles, I talked about open directories with Fofa/AI and the hunt for open-directory websites used by possibly malicious actors (or bug hunters/pentesters). In this new article, I’ll focus on the different ways to identify C2 infrastructures. There are many ways to identify these infrastructures, mostly thanks to TLS certificates, but also with service banners, HTML responses, and so on. Let’s delve into it!
Censys 101
Let’s begin with the basics. Since Censys offers a labeling feature for hosts scanned across the internet, there is, for a first approach, no need for a complex query. For example, by using this request:location.country=`France` and services.software.product=`Cobalt Strike`
You can already highlight some Cobalt Strike C2 hosted in France.
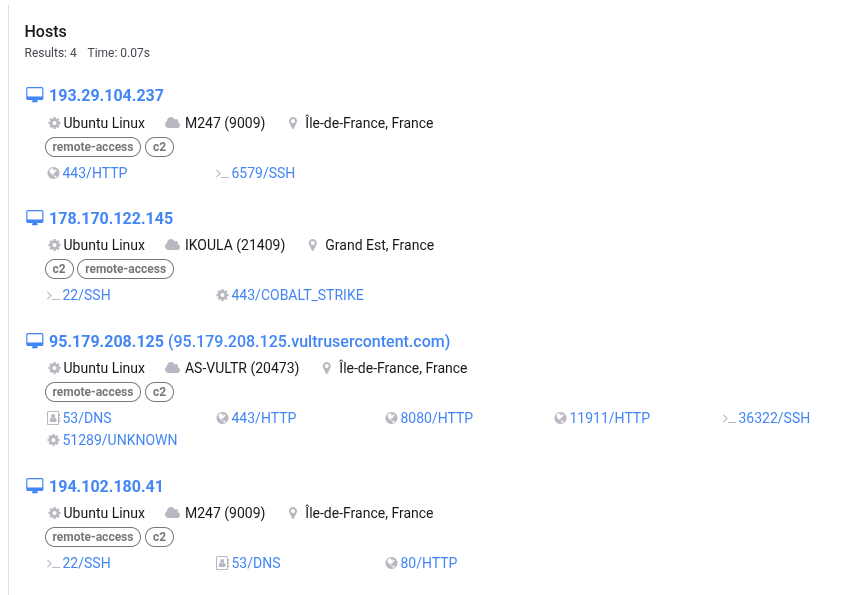
For this first example, only 4 results. In these 4 results, only 3 differents AS:
- M247 -> Romanian webhosting / Digital services
- IKOULA -> French webhosting services
- AS-VULTR -> US-Cloud Provider
A quick search with threatfox gives us results from one ip address: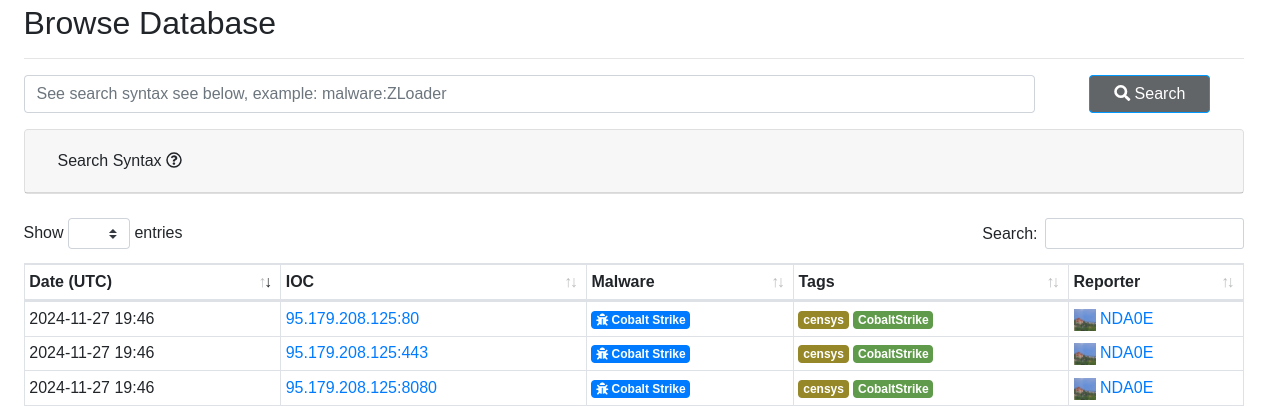
Threatfox is very interesting because it’s offering some stats about the AS. You can find others intersting rankings here.
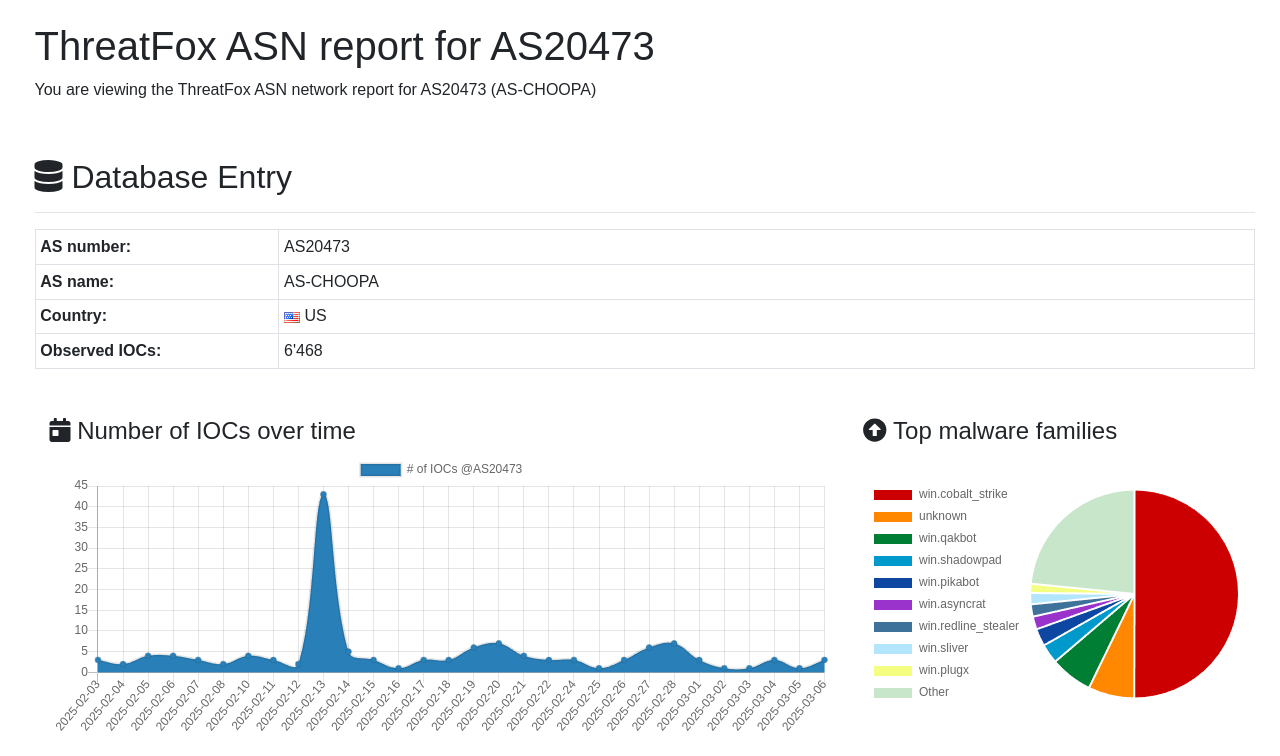
For the IOCs detected on this AS, we can see that mostly of them are Cobalt-Strike related.
Certificate fingerprint
The way to detect C2 with a default/minimal configuration is by using the TLS certificate fingerprint. Here, for this first research, two certificates have been detected:87f2085c32b6a2cc709b365f55873e207a9caa10bffecf2fd16d3cf9d94d390c and 496e6a15cd17ac972c547bca9fe6e61e08c7988ef6b24a99da15a2f63bbded85 the first one is the Cobalt Strike default, the second one is a custom. So with a research like: services.tls.certificate.fingerprint_sha256= `87f2085c32b6a2cc709b365f55873e207a9caa10bffecf2fd16d3cf9d94d390c we can identify all Cobalt Strike servers with the default TLS Certificate, but with a malleable C2 profile or a customization this fingerprint will change.
Let’s get back to open-dir…
Let’s make the following request: labels:`open-dir` and services.http.response.body:`exploit` and services.http.response.body:`payload`
I found this: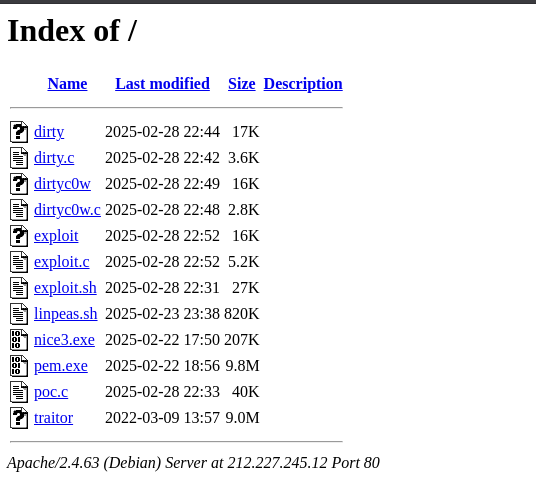
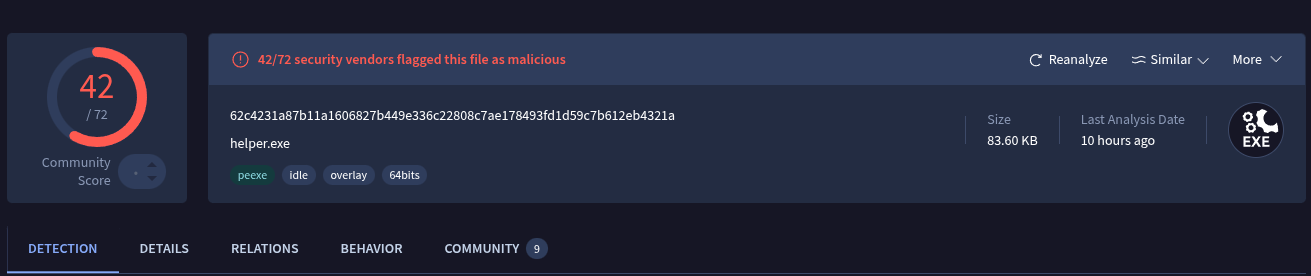
There is somes executables in there, let’s take one of them and make a dynamic analysis. As we can see, the downloaded executable is trying to communicating with another server:
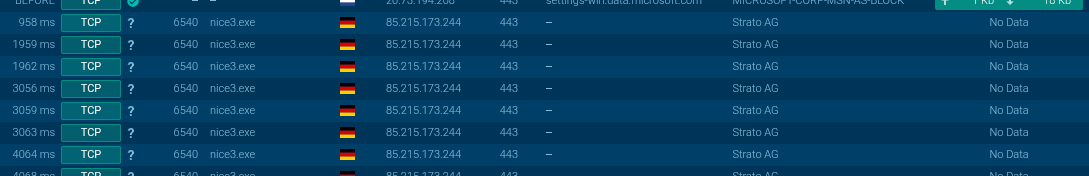
On this server, some useful tools:
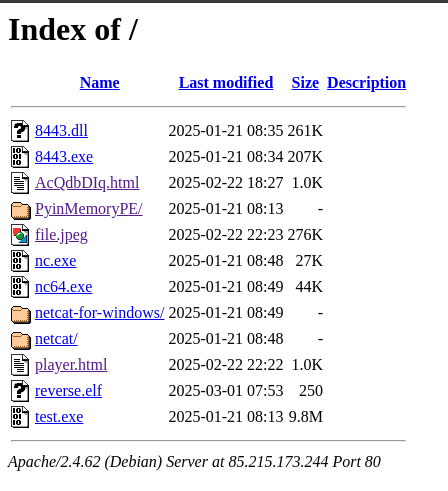
There is a second file: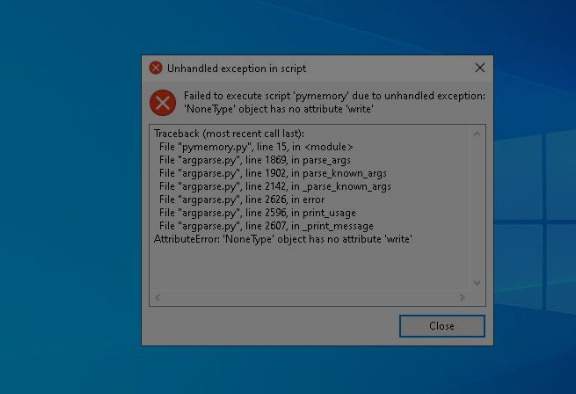
This one is using a tool in order to execute a PE in memory, filelessly. All these actions are related to a Metasploit C2. Well, there is a screenshot—it seems like a cybersecurity engineer or student is doing some tests… and getting help with DeepSeek. A Red Team operator preparing a Rubber Ducky physical attack? Well, a Red Team operator should erase proofs and tests if they want to stay under the radar…!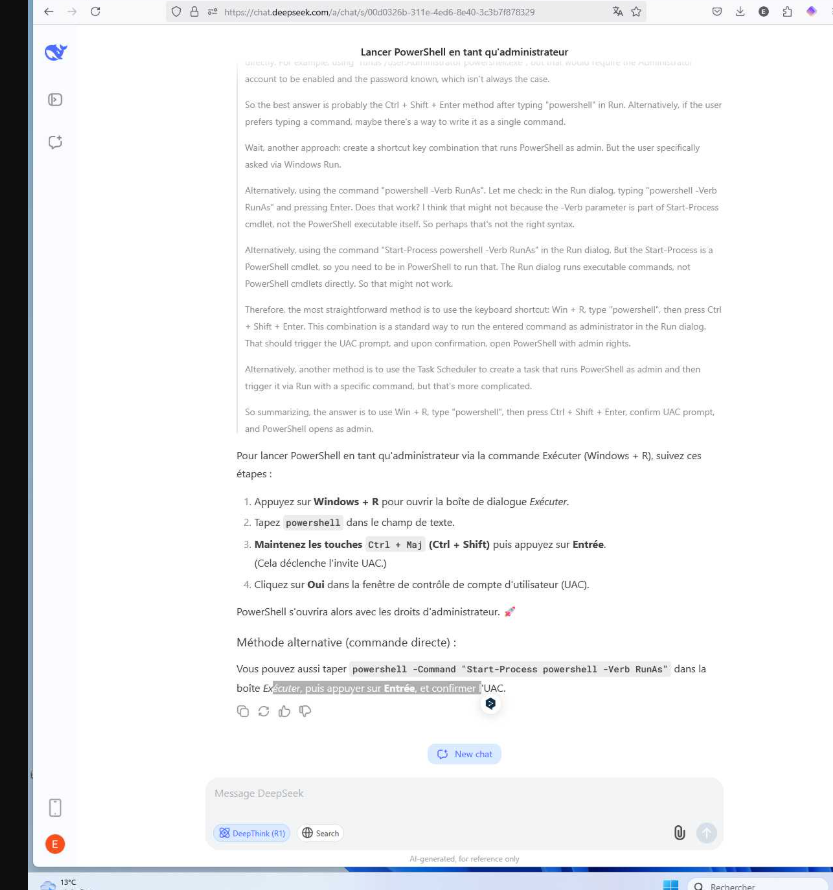
Unknown threat
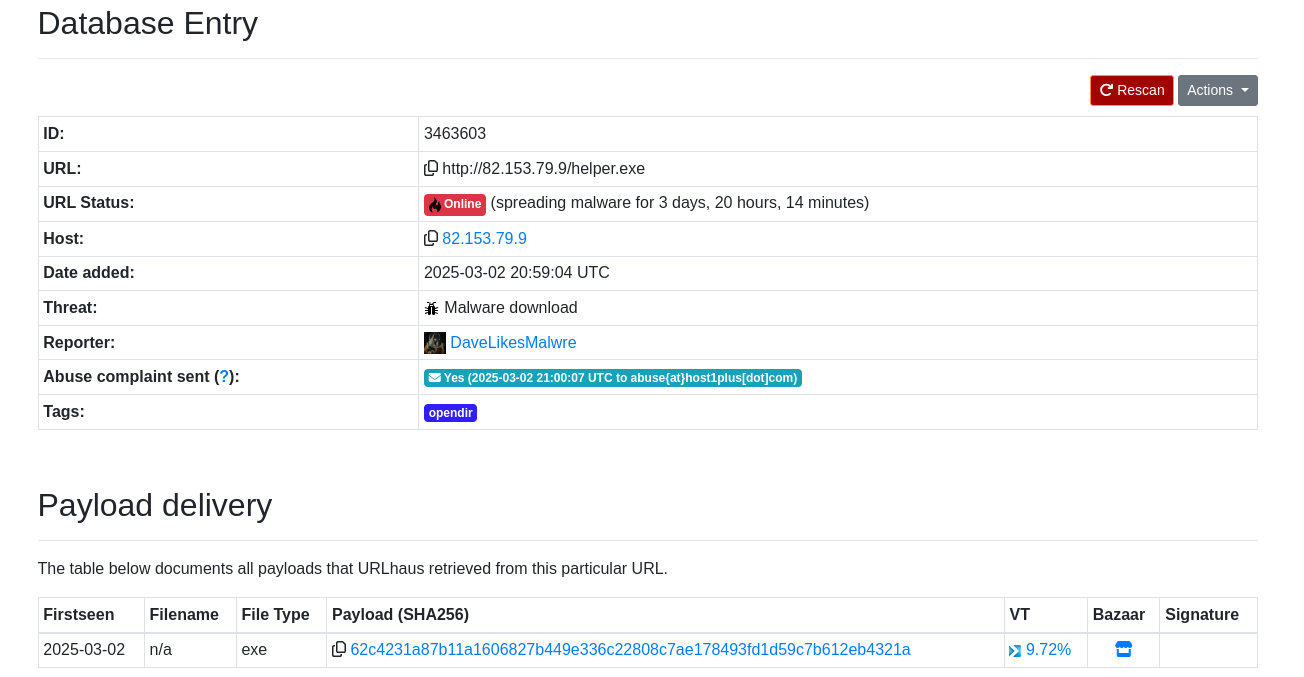
For this hunt, I looked for open-dir and c2 servers via the label feature. I came out with a malicious server hosting a .bat and a .exe…
The bat files is just downloading the .exe file and use a persistence mecanism:
1 | powershell -WindowStyle Hidden -Command "Start-Process notepad -WindowStyle Hidden" |
It seems like the threat is known on the platforms:
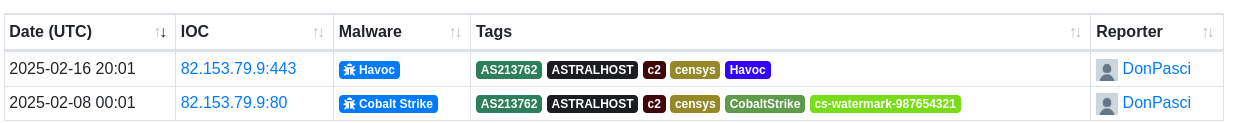
On the ANY.RUN sandboxe I couldn’t detect if it was a Cobalt Strike or Havoc related threat.
Looking for some sliver C2!
Well, after Cobalt-Strike and Metasploit… Let’s try to identify some Sliver C2! For this one I used a TLS cert fingerprint, I found an interesting server:
- Hosting an open-dir with a python server (hello: python -m http.server …)
- Openned port with default sliver TLS cert…
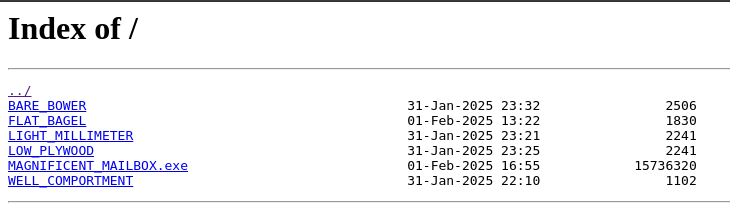
There is few interesting files, including “MAGNIFICENT_MAILBOX.exe”… This IP address seems to be already reported to threatfo obviously: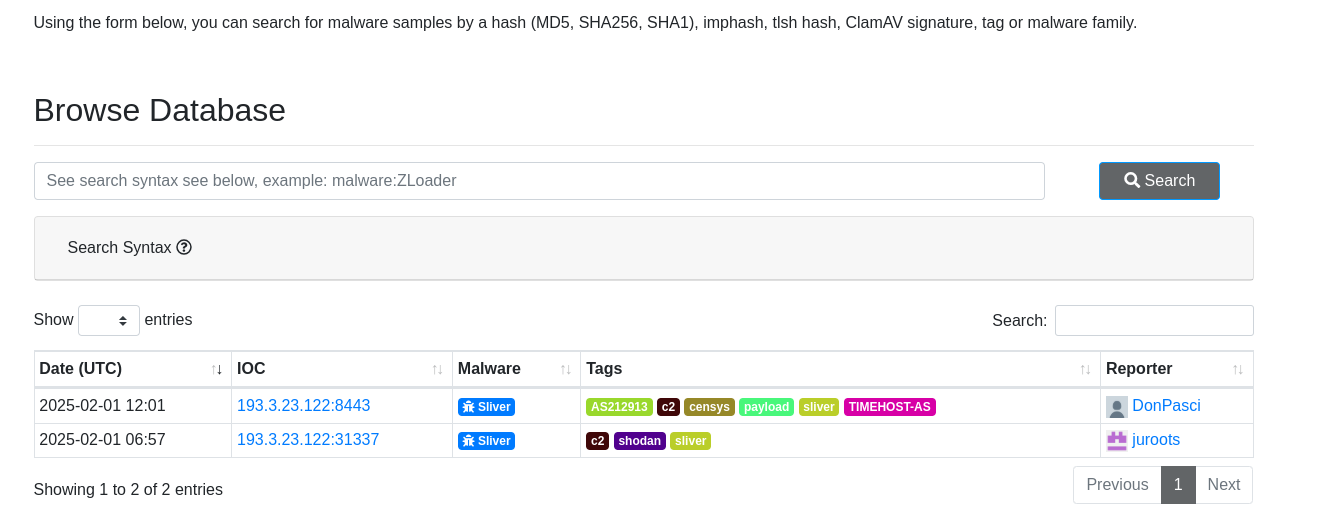
Conclusion
Hardening and changing the initial configurations of C2 infrastructures is necessary in order to avoid detection. The analysis of files contained in open-directory servers could highlight the C2 server. This kind of research is very interesting because it allows me to analyze techniques used by people on the red side. Even if it’s only for testing or educational purposes, techniques are evolving, and the analysis of executable files and configuration files provides a better understanding.