Let’s having fun!
A few months ago, a new feature was released by the Censys team: the label ‘suspicious-open-dir’! This label allows us to spot possibly malicious open directories. Quite interesting, isn’t it?Here is the documentation about it on the censys website
Before this feature, I used a combination of the open-dir label, the HTTP body response, and the server type (people seem to love python -m http.server… :D). Censys-GPT helped me a lot, to be honest.
I think this feature is going to reduce false-positive results and obviously make our requests shorter than before.
Intro: A hunting journey w/ Censys
So I used this request in order to find suspicious opendir hosted by Python webserver…
1 | labels=`suspicious-open-dir` and services.software.vendor=`Python Software Foundation` |
Some people use Python’s http.server to host a quick web server. Some of them even do it directly in their user home directory, which allows us to access bash history files and other interesting files. :D
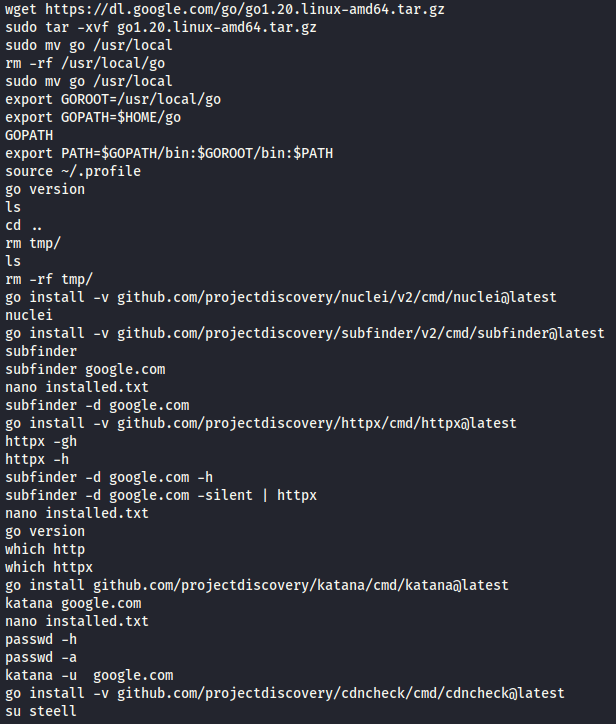
Few files relatives to sudo vuln & PwnKit
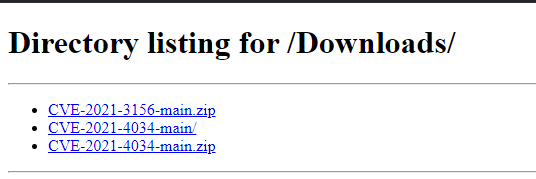
Here some PoC for recents exploit: whatsupgold,SolarWinds Web Help Desk, Fortra’s GoAnywhere
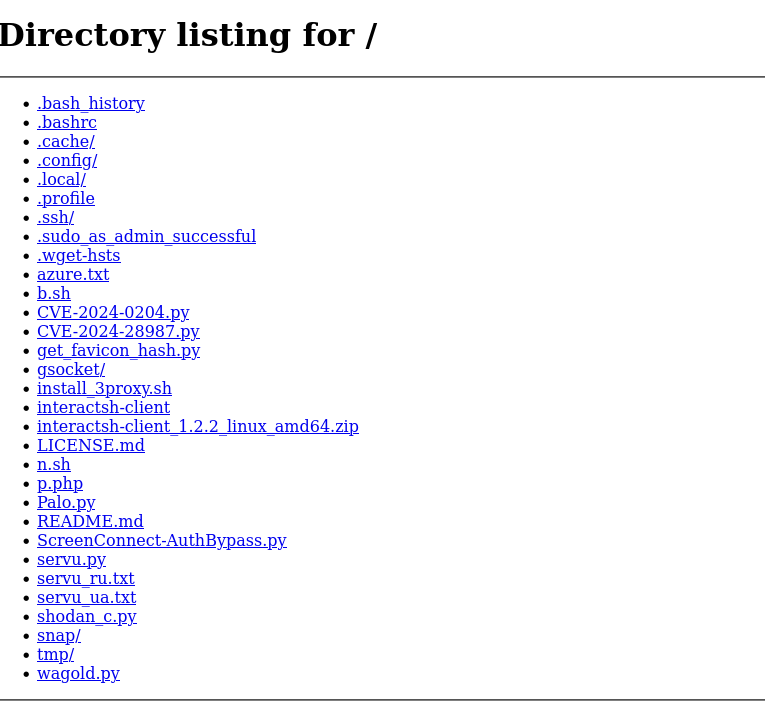
Payloads and funny things: Cobalt strike stuff
I Found some funny stuff on a server hosted at 20[.]83[.]148[.]22…
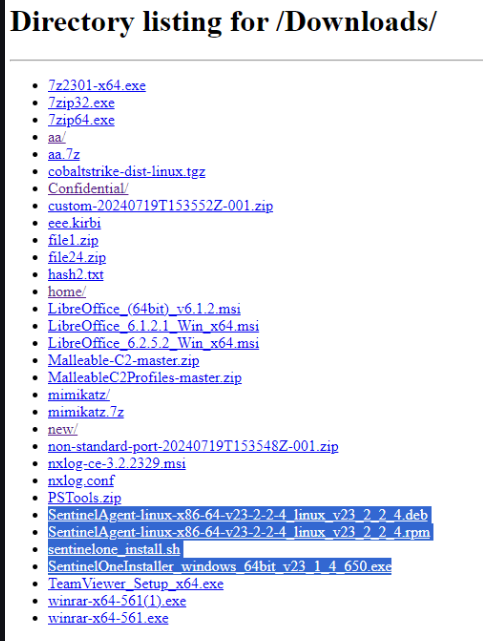
A Cobalt Strike Installer, Cobalt Strike profile, mimikatz, nxloook, PSTools, S1 EDR Agent installer, this IP address appears as IOC on ThreatFox DB.
This is the end of this first article (quite short isn’t it ????).